Kangana Ranaut, who is renowned for voicing her opinion without holding back, recently took aim at Punjabi artist Shubh for what she saw to be praising…


Kangana Ranaut, who is renowned for voicing her opinion without holding back, recently took aim at Punjabi artist Shubh for what she saw to be praising…

Veteran Pakistan cricketer Shoaib Malik has married Pakistani actor Sana Javed amid rumours of his divorce from Indian tennis legend Sania Mirza …

China’s lighting industry is a leader in technological innovation. This has been largely influenced by advances in moulding technology. Injection mold China, in particular, has set new standards for the lighting industry by becoming a cornerstone of the production. This article examines the role that injection molding plays in the development and production of lighting components in China. It highlights how it promotes innovation.
Injection Mold China revolutionized the production process of lighting components. The advanced technology allows the manufacture of intricately designed components that meet precise specifications. Injection moulding’s adaptability and versatility allows manufacturers to meet the changing demands of the lighting sector, creating components that are both aesthetically pleasing and functionally superior.
The increased design flexibility that injection moulding offers is one of the main benefits. This technology allows for the creation of complex forms and shapes, which were difficult to achieve with traditional manufacturing methods. The injection mold China technology has enabled designers to push their creativity boundaries, leading to lighting components with innovative designs and functionally effective functions.
Injection moulding is the best way to achieve both precision and durability in lighting components. This ensures each component is manufactured to the highest accuracy, resulting in better fit and functionality. The durability of the materials used in injection molding contributes to the long-term sustainability and cost-effectiveness of lighting products.
Collaboration between lighting manufacturers, and injection moulding companies, is essential to driving innovation within the industry. Utilizing injection mold China, these companies specialize in producing high quality components that meet industry standards. The expertise of these companies in handling complex moulds and diverse materials is crucial in developing advanced lighting solutions.
Injection moulding plays a key role in the future of lighting component production in China. The future of this industry is shaped by emerging trends, such as the use eco-friendly materials and integration of smart technology, along with the development of energy efficient lighting solutions. Injection mold China has the ability to adapt to this trend, and ensure that the lighting industry is able to continue to innovate.
The importance of moulds in the creation of efficient lighting components in China is not to be underestimated. Injection mould China has played a major role in the advancement of the lighting industry. It offers unparalleled design flexibility, accuracy, and durability. This progress is further enhanced by the collaboration with plastic injection molding companies, which leads to innovative and efficient lighting products. Injection moulding’s role in shaping the future of the lighting industry is crucial as it evolves. It illuminates the path to more advanced and sustainable lighting technologies.

Handles are often overlooked in the retail industry where security and customer experience are of paramount importance. These small fixtures have the potential to make a big difference in terms of accessibility and security.

The gaming industry has experienced significant change in the past few decades, going from an era of arcade cabinets and home consoles to the digital age of mobile gaming.

In current years the sector of medication has witnessed a revolutionary transformation with the advent of telemedicine This technological evolution has not most effective bridged geographical gaps however has also performed a pivotal position in improving affected person care throughout various specialties One such domain wherein telemedicine has proven to be a recreation-changer is orthopedics.
If you are looking to become a supplier of Orthopedic Implants in Saudi Arabia find experienced trauma implant manufacturers.
What is the Role of Telemedicine in the Field of Orthopedics?
Enhanced Accessibility for Orthopedic Care
Orthopedics the department of medication that makes a speciality of the musculoskeletal device deals with a myriad of conditions starting from fractures and joint injuries to continual problems like arthritis Traditionally orthopedic consultations worried in-person visits to clinics or hospitals regularly accompanied by using lengthy waiting instances However telemedicine has redefined the panorama of orthopedic care bringing approximately blessings that expand a ways beyond comfort.
Overcoming Geographic Barriers
One of the number one advantages of telemedicine in orthopedics is the accessibility it offers to sufferers. People dwelling in far flung regions or those with mobility issues can now without problems hook up with orthopedic specialists with out the want for big tour. This not only saves time and sources however additionally ensures that individuals acquire well timed care, vital in situations wherein spark off intervention could make a large distinction in outcomes.
Post-Operative Care and Rehabilitation
The role of telemedicine turns into especially critical in publish-operative care and rehabilitation Through digital consultations orthopedic surgeons can remotely display a affected person’s progress investigate rehabilitation physical activities, and offer important steerage This no longer only empowers patients to actively participate in their recuperation but additionally reduces the want for common, frequently traumatic, in-person visits.
Managing Chronic Conditions with Virtual Consultations
Another factor in which telemedicine shines in orthopedics is its effectiveness in coping with continual situations which includes osteoarthritis and rheumatoid arthritis Regular observe-usacan be conducted via virtual channels permitting orthopedic professionals to assess signs and symptoms, alter medications and provide lifestyle guidelines This proactive technique to continual disorder control contributes to better long-term outcomes and stepped forward fine of life for patients.
Effective Emergency Response
Orthopedic emergencies including fractures or dislocations also benefit appreciably from telemedicine. Through video consultations, orthopedic surgeons can quick examine the severity of accidents, manual sufferers on immediately first resource measures, and determine the need for in-person care. This actual-time interaction can be a lifeline, especially in situations where instantaneous scientific interest is crucial.
Interdisciplinary Collaboration through Virtual Platforms
Orthopedic telemedicine is not simply constrained to consultations; it extends to collaborative efforts amongst healthcare specialists. Orthopedic surgeons can effortlessly collaborate with primary care physicians, physical therapists, and different professionals via digital platforms, making sure a comprehensive and integrated technique to patient care. This interdisciplinary collaboration complements the general exceptional of orthopedic offerings, providing patients with a extra holistic and personalized treatment plan.
Despite the numerous benefits it’s far vital to acknowledge that telemedicine in orthopaedics also poses certain challenges Physical examinations and diagnostic exams like X-rays or MRIs as an example can’t be carried out remotely However improvements in wearable generation and home-based tracking devices are steadily mitigating those demanding situations allowing for a more complete virtual evaluation.
In end, telemedicine has emerged as a transformative force inside the area of orthopaedics, supplying accessibility, performance, and advanced patient outcomes. As era keeps to conform, the integration of telemedicine into orthopaedic exercise will likely end up even extra seamless, similarly improving the transport of care to people with musculoskeletal situations. The marriage of generation and orthopaedics exemplifies the capacity for innovation to reshape traditional healthcare paradigms, in the end benefiting both patients and healthcare vendors.
Know more about emerging healthcare technology and explore the latest medical healthcare products & supplies at the Arab Health Dubai 2024.

As the temperature drops and iciness units in it’s essential to pay greater interest to our bone health The bloodless weather coupled with decreased exposure to daytime can effect our bones and joints Maintaining wholesome bones in some unspecified time in the future of wintry weather calls for a combination of dietary alternatives bodily hobby and manner of lifestyles modifications In this blog we are able to discover 5 practical pointers to help you hold your bones robust and resilient within the path of the bloodless season.
If you are looking to become an Orthopedic distributor in Dubai connect with the leading orthopedic manufacturers.
Winters
Winter regularly technique a good deal much less exposure to daylight, a primary supply of food plan D. This essential weight-reduction plan performs a critical feature in calcium absorption, promoting robust and wholesome bones. To fight the iciness blues, try and spend a while outside during daylight hours. If this isn’t feasible, undergo in thoughts incorporating nutrients D-wealthy meals into your food plan. Fatty fish like salmon and mackerel, fortified dairy products, and egg yolks are extremely good resources of vitamin D that would make a contribution to bone fitness.
Calcium is a key mineral for bone health, presenting the structural useful resource our bones want. During wintry weather, make a conscious attempt to consist of calcium-wealthy elements to your diet plan. Dairy products which include milk, yogurt, and cheese are conventional alternatives, but if you’re lactose intolerant or take a look at a plant-based completely diet, maintain in thoughts fortified plant milks, leafy inexperienced vegetables, and nuts. Aim for the recommended each day intake of calcium to make certain your bones stay strong and resilient.
Hydration is regularly ignored while discussing bone health however it performs a vital function in maintaining the integrity of our bones Proper hydration guarantees that our joints and cartilage stay lubricated decreasing the chance of fractures and accidents. During winter we have a tendency to consume hotter liquids so take some time to include water, natural teas and broths to your everyday routine Limiting the consumption of caffeinated and sugary beverages may additionally moreover even make contributions to better bone health.
The less warm weather might deter you from out of doors sports, however it is important to stay physical lively for top-quality bone health. Engage in indoor sports activities activities that target weight-bearing and power schooling. Activities like yoga, Pilates, and resistance training can assist hold bone density and versatility. If venturing outdoor is not appealing, keep in mind turning into a member of a close-by gymnasium or taking part in digital health training to preserve your bones and joints in top shape.
Winter is notorious for bringing an array of ailments, and a weakened immune tool cannot immediately have an effect on bone health. Ensure your immune system is performing at its tremendous by the use of incorporating immune-boosting meals into your weight loss program. Foods wealthy in vitamins C and E, which incorporates citrus end result, berries, and nuts, can help assist your immune device. Additionally, prioritize getting right enough sleep and managing stress, as each elements make contributions to ordinary properly-being, which includes bone fitness.
Maintaining healthful bones in the course of wintry climate calls for a holistic method that mixes nutritional picks, physical interest, and way of lifestyles modifications. By embracing diet plan D, prioritizing calcium-wealthy food, staying hydrated, carrying out indoor workout, and boosting your immune tool, you may ensure that your bones stay sturdy and resilient at some level within the less heat months. Remember, a proactive technique to bone fitness will no longer simplest benefit you during wintry weather however will make a contribution in your everyday nicely-being all 365 days round. Stay warm temperature, stay energetic, and prioritize your bone health for a greater wholesome, happier you.
Check out a CE-certified range of orthopedic implants like LCP Locking Compression Plate, Variable Angle Plate, and others from Siora Surgicals Pvt. Ltd.

A Rs. 1 crore health insurance policy often covers critical illnesses. This is particularly crucial as the incidence of severe health conditions is on the rise.

Thinking about getting your kids to learn Chinese? Whether it’s for an upcoming trip, career, or simply because you have family connections to China, it’s worth considering. With over a billion people speaking Chinese, it’s a language that opens up plenty of exciting opportunities worldwide. Learning it is not just cool but also a really useful skill to have.
Even if your kids aren’t going to the office anytime soon, picking up Chinese now can be a smart move for their future. It’s like giving them a cool tool that might come in handy down the road. The language holds significance in the business world, and you never know how it might positively impact their future endeavors.
Learning Chinese offers a fascinating and, admittedly, a bit challenging language experience for your children. So, let’s delve into ways to inject excitement and enjoyment into the learning process, making sure that mastering Chinese becomes a fun adventure for kids of all ages.
It’s like decoding a secret language that goes beyond mere words. Mastering Chinese isn’t just about speaking; it’s a journey that reshapes the way the brain thinks, fostering creativity and honing problem-solving skills.
Key benefits your kids can enjoy by mastering Chinese:
Learning Chinese isn’t just a linguistic feat; it transforms kids into adept problem solvers. Tackling the complexities of a new language encourages thinking outside the box, cultivating creativity and critical thinking. For example, when deciphering unfamiliar characters, children learn to approach challenges with innovation.
The process of memorizing Chinese characters and words becomes a memory-boosting exercise. As your kids progress through school and university, enhanced memory skills gained from learning Chinese will aid them in various academic pursuits. For instance, recalling intricate characters can be compared to solving puzzles, enhancing overall cognitive abilities.
Chinese is a gateway to a treasure trove of history and captivating traditions. As your kids learn the language, they’re setting out on a cultural discovery journey. Delving into Chinese traditions and history not only expands their knowledge but also ignites a curiosity that can foster a passion for exploring the world. As they grow, this cultural awareness becomes a foundation for their worldview.
Becoming fluent in Chinese can be a valuable asset, distinguishing your kids in the future job market. Even though they might be years away from joining the workforce, establishing a foundation in Mandarin can be a strategic move. It unlocks various career opportunities, providing them with a head start in an ever more interconnected world.
Chinese, with its distinctive tones, transforms language into a musical experience. Speaking Chinese is akin to singing, adding a unique and enjoyable dimension to communication. Encourage your kids to embrace the melodic nature of the language, turning the learning process into a delightful adventure.
Teaching Chinese to kids requires age-appropriate strategies that blend education with enjoyment. Here’s a breakdown of effective approaches for various age groups:

Teaching your kids Chinese at home doesn’t require you to be a language expert.
Beyond the language-learning apps, videos, and games we’ve talked about earlier, consider exploring the option of online tutors. These tutors specialize in making the learning experience enjoyable and rewarding for your kids.
Imagine having a dedicated Chinese language tutor who guides your children through the language journey, providing personalized lessons and interactive sessions. This not only adds a dynamic aspect to their learning but also offers a supportive environment for questions and clarification.
For instance, you can connect with a qualified Chinese language tutor who tailors lessons to your child’s proficiency level and interests, incorporating engaging activities, conversations, and exercises that align with your child’s learning style. This ensures a more effective and enjoyable learning process.
So, if you’re not confident about your own Chinese language skills, an online tutor becomes a valuable resource to facilitate your kids’ language education in a way that is both fun and fulfilling.
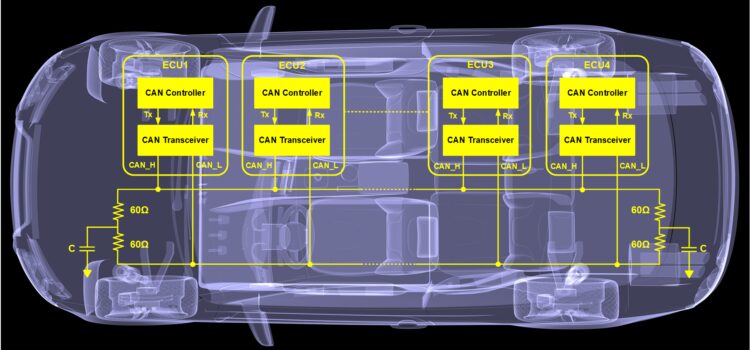
Canbus Modules /technology is reshaping the automotive industry, transforming vehicle operations and communication. At the core of this transformation are canbus module.